What is Privacy coin and how does it work? Table of Contents
What is privacy coin and how does it work?
Cryptocurrencies are highly regarded for the anonymity provided through services such as decentralized transactions. After Bitcoin (BTC) was created, various cryptocurrencies with the characteristics of Bitcoin were born.
However, in blockchains with cryptocurrencies like Bitcoin, decentralized transactions and anonymity exist, but are not completely private. This means that any BTC used in a transaction can be traced through previous transactions.
This situation has created an untraceable and completely private cryptocurrency. These cryptocurrencies are called Privacy Coins. In this post, we will explain what a privacy coin is, how it works, and what are its main features.
3 Best Cryptocurrency pairs to trade
What is Privacy coin?
“Privacy Coin” is a coin that does not provide information about cryptocurrency transactions. One reason privacy coins were created is to take people’s privacy rights and apply them to other digital transactions or digitalized decentralized services.
The second reason is that cash must also be digitized. When cash is deposited into a bankbook, it is necessary to use cash in decentralized transactions as it cannot be tracked unless it is purchased through that account. Therefore, using privacy coins advances blockchain technology with built-in functions of cash.
Another reason is fungibility: one coin is exactly like another. For example, when bitcoins are used for illegal transactions, they become “contaminated”. Because Bitcoin can be traced. And if you owned those tainted bitcoins, it would be difficult to sell those bitcoins as most people wouldn’t accept a bitcoin with that history. However, Privacy Coins are not trackable. Therefore, even if a coin was used for illegal transactions, the coin is like any other coin regardless of its history.
Two key elements of a privacy coin are anonymity and untraceability.
Anonymity is the hiding of a user’s personal information (ID) from any decentralized transaction or service. Traceability is what makes transaction information untraceable from third parties. Because of these two factors, privacy coin trading is banned in some countries, including South Korea. While the nature of privacy coins may seem mysterious, privacy coins are growing both in terms of community and value.
The most famous coin is privacy dashboard include (Dash), by Claude Monet (Monero), if the cache (Zcash), Beam (Beam), father (Verge), Green (Grin).
Before we dive into what makes these cryptocurrencies special, let’s briefly review how privacy coins work.
Start Investing in Cryptocurrencies
How do privacy coins work?
Like other cryptocurrencies, Privacy Coin works through blockchain technology. Since all transactions are decentralized, there is no need for a third party to regulate them.
Transactions are verified by nodes that are part of the network . To verify these transactions, nodes must solve complex mathematical problems to prove that the transactions are valid. When a transaction is confirmed, information is added to the blockchain, and other nodes also update the information.
Agreed mechanisms, privacy coin proof-of-work (PoW: Proof-of-Work ), shares proven : Use a hybrid version, or a work certificate and proof of ownership (Proof-of-Stake PoS) . Each privacy coin differs from other cryptocurrencies in terms of functionality. These differences make Privacy Coins “private”.
Here are the main strategies used by Privacy Coins:
1. Stealth Addresses
As the name suggests, stealth addresses mean privacy. Each time you receive a coin, a new address is created so others cannot use your address. This is one of the simplest ways to ensure the privacy of a blockchain.
Some privacy coins use a more complex stealth address model. This is called the dual-key stealth address protocol (DKSAP). Each user on this blockchain will have a private view key, a private spend key, and a recipient address. The recipient address is the only address visible to other users during a transaction. However, the coins you receive will not go to the recipient address, but to another unique, private address on the blockchain. A private send key is used to send cryptocurrencies. A private temporary key (private view key) is used to verify the funds being received.
2. Ring Signatures
Ring signing is another way to ensure privacy. When you sign a transaction with your private key, other users can easily link to your address with that signature. Ring signatures prevent this from happening. Since many signatures are done through a random signature “ring” that co-signs the transaction, it becomes more difficult for others to associate the transaction with your address. The larger the ring of signatures, the more private your address will be.

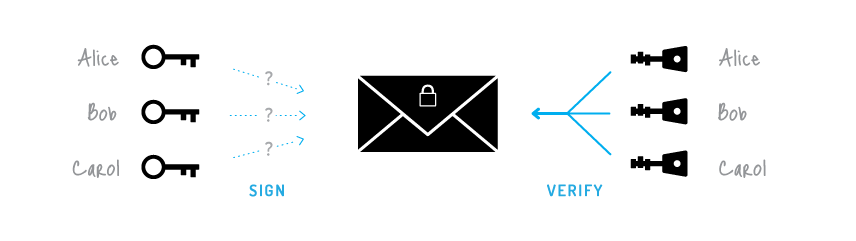
In addition to ring signing, one way to provide more privacy, depending on the model, is Ring Confidential Transactions (RCTs). Just as addresses are made private using ring signatures, so are the amounts associated with those transactions.
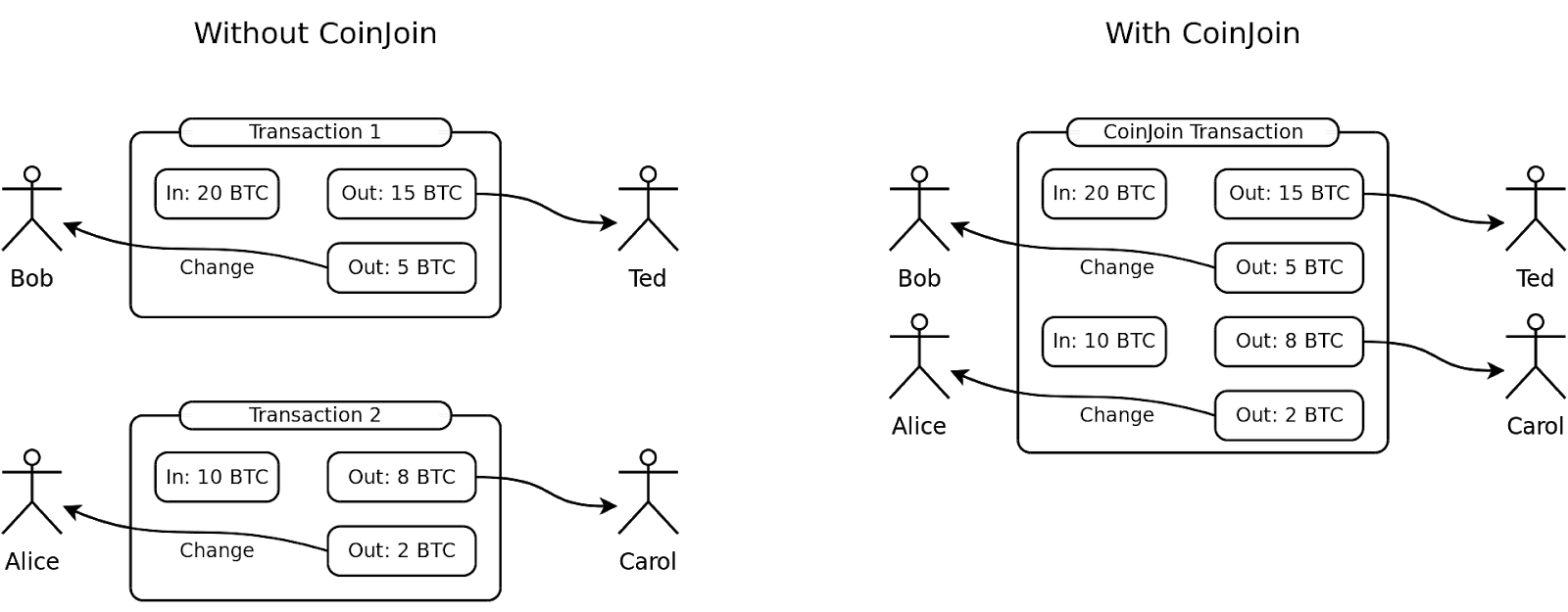
3. CoinJoin
Coinjoin is a method of combining different transactions into one larger transaction. Then, a custodian using an address that has never been used takes the coins and distributes them to the desired recipients as the senders initially started.
4. Zero knowledge Snark (zk-SNARK)
Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk-SNARK) is a technology modified to apply the existing zero-knowledge proof in a more succinct and non-interactive environment. Transactions on the blockchain can be verified or verified without requiring transaction details such as sender or recipient addresses. In this way, transaction information is kept private. This model of validating transactions has proven useful in terms of blockchain scalability.
5. Mimblewimble
Mimblewimble is a relatively new method used to ensure privacy. Mimblewimble also provides a new model of blockchain, with many cryptocurrencies starting to implement Mimblewimble on their own blockchains. Each information block consists of output, input, and signature information. A transaction simply checks that the input and output are the same. In this simple and efficient way, Mimblewimble maintains the privacy of the blockchain.
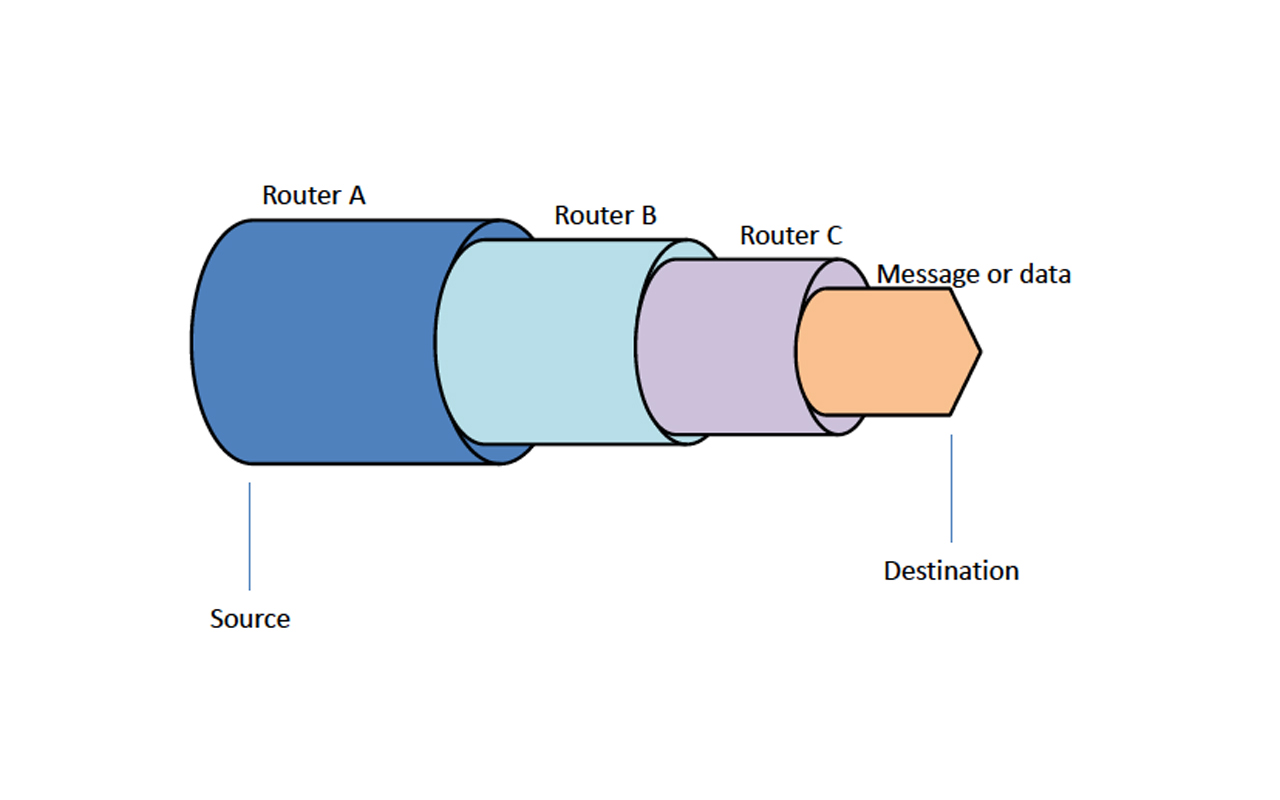
6. Tor (anonymous network)
TOR (TOR) is similar to the onion. Hence the name onion routing, or “onion routing,” which encrypts IP addresses through various layers of encryption.
Which is the Best Cryptocurrency to buy in 2021?
Advantages and disadvantages of privacy coins
So far, we have discussed the main characteristics of privacy coins that increase the level of privacy in cryptocurrencies. However, like all cryptocurrencies, privacy coins have their pros and cons.
Advantages of privacy coins
- Privacy
- Of course, privacy is the biggest advantage. Privacy Coin users are protected from those who want to know more about cryptocurrency transactions.
- Financial security
- Businesses and governments continue to track people’s financial data. As a result, more and more people are turning to cryptocurrencies as a way to avoid such tracking. Although Bitcoin and other altcoins provide financial security in a decentralized way, they do not provide the same financial security as privacy coins because all transactions are publicly viewable through the blockchain.
- Same as cash
- Just as cash is untraceable, privacy coins are untraceable. Direct transactions using cash are one of the safest and easiest ways to do so, so privacy coins, like digital cash, process transactions in a decentralized way.
Disadvantages of privacy coins
- Exploit
- The biggest downside of privacy coins is that they can also be used for illegal activities. You can also use your Privacy Coins to buy illegal goods on the black market. It can also be used for money laundering or tax evasion.
- Government sanctions
- Because Privacy Coins can be misused in a variety of ways, the use of Privacy Coins is prohibited in some countries. Whenever a country bans the use of Privacy Coins, the price can drop sharply. This situation adversely affects investors.
- Transaction fee
- Privacy coins typically have slightly higher transaction fees than other cryptocurrencies due to the fact that they have privacy features that other cryptocurrencies’ blockchains do not have.
Cryptocurrency Trading – Best Strategies
Most Popular Privacy Coins
What are some privacy coins with the characteristics we have mentioned so far?
1. Monero
As one of the largest privacy coins in the cryptocurrency market, Monero uses Proof-of-Work (PoW) as its consensus mechanism. For the privacy model, Monero uses both Ring Confidentiality Transactions (RingCT) and stealth addresses.
The US Internal Revenue Service awarded a $625,000 bounty to any organization that can address Monero’s privacy technology. Coin Telegraph, according to the widely Che System (Chiainalysis) and Integra FEC (Integra FEC) are two companies that are successful in receiving a reward to present a solution.
2. Dash
Dash is another privacy coin that has grown in recent years. It is a Bitcoin fork, meaning that many components of Dash and Bitcoin are identical. The difference is that Dash consists of a hybrid version that uses both Proof of Work (PoW) and Proof of Stake (PoS).
Dash uses PrivateSend and InstaSend for transactions. Every “round” of private sand is equivalent to processing one coinjoin transaction to distribute coins to one recipient. Instasend is a Dash feature that is much faster than Bitcoin transactions.
3. Zcash
Zcash (ZEC) is also a Bitcoin fork. It uses proof-of-work (PoW) as a consensus mechanism. Zcash uses zero-knowledge proof (zk-SNAK) as a privacy mechanism, which keeps the amount, sender, and recipient addresses private from anyone unrelated to the transaction. Unlike other privacy coins, in Zcash, privacy features are optional and users can decide which transactions are made private.
4. Verge
Verge (XVG) is also a privacy coin that has been proven to effectively maintain privacy. In 2014 it was named Dogecoin Dark, but two years later it was rebranded as Verge. Verge uses Tor (or onion routing) as its privacy mechanism. In Verge, your IP address is encrypted at multiple layers, so other users cannot crack it.
5. Beam
Beam is a privacy coin that uses Mimblewimble as a privacy mechanism. This privacy model is relatively new and simple compared to other blockchains. Each block consists of output, input, and signature information, while other information remains private. Beam also uses Dandelion++ as a mechanism to ensure anonymity.
6. Green
Like Beam, Green uses Mimblewimble to ensure the privacy of the blockchain. Green is considered one of the best privacy coins in terms of scalability.
It differs from other cryptocurrencies in that everyone is equally rewarded for mining. It is expected that these characteristics will not change in the future, so miners today may receive the same rewards as miners 50 years from now.
Conclusion
Now that everything about privacy coin is different, what can we conclude?
As many hackers are looking for the privacy of cryptocurrency users, ensuring privacy in cryptocurrency is very important. Privacy Coins exhibit the attractive side of complete privacy guarantees and traceability.
The dark side of privacy coins is that they have been used for tax evasion, money laundering, and the purchase of various illegal goods. Programmers will find a way to prevent the use of Privacy Coins for illegal activities while maintaining complete privacy. While we may not be able to figure out how to do this right now, the future of privacy coins looks bright.




Comment by cryptoloversofxm
February 19, 2025
I just saw that XMTrading now supports cryptocurrency deposits and withdrawals. No fees, instant transactions, and up to $30K per month. Each deposit gets a unique wallet addres...